- While the recent Chinese balloon incident in the US attracted significant public attention, the broader picture indicates that such an incident is only the tip of the iceberg.
- A survey conducted by the Centre for Strategic and International Studies (CSIS) suggested that espionage activities are notably on the rise.
- Chinese intelligence-gathering activities mainly include industrial, nuclear, cyber and academic espionage.
- China’s upper hand in cyber espionage vis-à-vis the US indicates a worrisome trend that is likely to remain one of the most focal points of bilateral contention between the two countries.
China and Southeast Asia 2023-1: Chinese espionage activities in the US

Towards the end of 2022, Sino-US bilateral ties finally started to signal some cautious steps toward a warming trend. However, this optimism soon dissipated, as the so-called “Chinese spy balloon” incident resulted in yet another serious challenge to Sino-US relations. Unlike before, this event attracted a huge degree of attention from the wider public, who closely watched how the incident unfolded; however, for the US government, such cases relating to Chinese espionage are not that surprising. Although China has long been involved in multidimensional espionage activities in the US, the recent Chinese increasingly sophisticated activities are becoming a major issue for Washington.
Since the founding of the People’s Republic of China, the US was long been the main target of interest for Chinese espionage activities. In fact, the first wake-up call for the US dates back to not far from the establishment of the PRC. In 1955, Qian Xuesen, a rocket scientist who worked on the Manhattan Project, was deported by the US back to China after five years of house arrest due to alleged links with the PRC. Subsequently, Qian became a Chinese national hero and is now referred to as the father of Chinese rocketry in space and missile programmes whose knowledge, acquired in the US, has been essential. However, it was only after Deng Xiaoping’s reforms that China began to pose a serious challenge to the US. With its growing capabilities and strength, China became the US’s main rival on a global scale and, as a result, the espionage activities increased greatly in both scope and complexity. The Centre for Strategic and International Studies (CSIS) conducted a detailed survey of Chinese espionage cases that took place in the United States between 2000 and 2023. The results suggest that espionage activities are on a notable rise: out of the 224 reported instances, 31% occurred within the years 2000 to 2012, while 69% of the cases occurred within the last ten years. This coincides with the beginning of Xi Jinping’s rule in China. With regards to the main actors involved and their intent, the results reveal the CCP’s multidimensional approach.
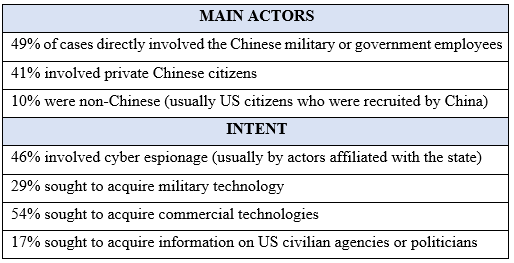
Figure 1. Main characteristics of Chinese espionage activity. Source: CSIS Survey of Chinese Espionage in the US
Attempts to increase mutual trust and reduce espionage activities had some initial success, but these were short-lived. As can be seen from the figure 2, the period from 2013-2016 marked a notable decline in espionage activities. The main catalyst behind such a change can be credited to the so-called “Snowden Effect”. The Snowden Leaks, which revealed the US National Security Agency’s (NSA’s) global surveillance network, was by far the most significant reason behind changes in the US-China dynamic on cybersecurity. On the one hand, it led the US to significant change how it safeguards privacy, while giving much more attention to cybersecurity (that in turn resulted in pressuring China with regards to cyber-attacks and cyber theft). On the other hand, these leaks were also a win for China, as from both economic and political standpoints, China stood to gain significantly from the global revelations about the NSA activities. In particular, China-related surveillance activities (hacking into the Chinese mobile phone companies, accessing the Tsinghua University servers, etc.) were used by the Chinese government, who criticised the US for hypocrisy and double standards.
Since the Snowden revelations, Sino-US relations have remained tense. The initial frustrations began soon after Snowden, when the then most-wanted US fugitive was allowed to flee Hong Kong. Snowden had planned to fight his legal battle there; however, as reported by Reuters, China persuaded Snowden to flee Hong Kong in order to avoid an extradition battle that would have a negative effect on bilateral ties. After the leaks, the US also began to pay much more attention to cybersecurity, and the Obama government hinted on several occasions that the team was drawing up economic sanctions to target Chinese companies and individuals that gained from cyber activities. Just before the 2015 Xi Jinping state visit, a large-scale cyber-attack occurred that acquired large amounts of US government personnel data, including security clearances.
The reduction in espionage cases, although temporary, can be accredited to the 2015 Xi official visit to the US. In a joint press conference at the time, President Obama stated that “Today, I can announce that our two countries have reached a common understanding on the way forward(…) We have jointly affirmed the principle that governments don’t engage in cyber-espionage for commercial gain against companies.” While this agreement was significant, Obama also did not avoid the use of harsher rhetoric and hinted at potential sanctions against China over cyber hacking in the future. However, even though the drop in espionage cases was notable, FireEye iSIGHT Intelligence, an authoritative cybersecurity firm, was not that optimistic: while it acknowledged a “notable decline” in China-related cybersecurity breaches, the report also noted that there was no evidence of a coordinated shift in the behaviour of China-based groups, but instead decline in cases that could be attributed to a change of tactics – namely, more sophisticated and stealthy methods.
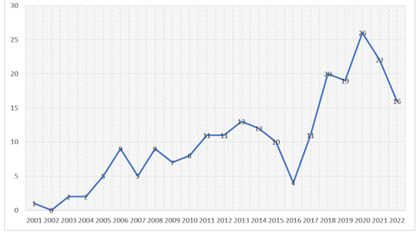
Figure 2. Chinese espionage cases in the US from a historical perspective. Source: CSIS Survey of Chinese Espionage in the US.
Types of Chinese espionage activities
Historically, Chinese activities in the US were much narrower and limited in scale. However, this situation changed drastically as the Chinese tools and means of penetration were significantly enhanced, making the overall scope of activities more wide and far-reaching.
a) Industrial espionage
Economic/industrial espionage has long been a major point of contention in Sino-US bilateral relations. Throughout Trump’s presidency, this type of espionage became even more prominent. Industrial espionage typically involves the stealing of commercial secrets by mid-level employees that are linked to the PRC. Recently, several high-profile cases were widely discussed, one of which regarded Xu Yanjun, an intelligence officer for the Ministry of State Security of the PRC, who was arrested while trying to steal jet fan blade designs from General Electric Power (GE). Similarly, Zhang Xiaoqing, a former employee of GE, was sentenced to two years in prison in January 2023 for hiding confidential files, including designs for gas and steam turbines, inside the digital photograph of a sunset. In another case, Charles Lieber, Head of Harvard University’s Chemistry Department and a pioneer f nanotechnology, was charged with accepting money from the Chinese government. This marks an important development, as a high-profile academic was caught between the Sino-US technological rivalry. This sphere of contention is also spilling into diplomatic grounds. In July 2020, the US requested the China close its consulate in Houston “in order to protect American intellectual property and American’s private information”. The threat posed by China has also been enhancing cooperation between the US and its allies. In July 2022, the heads of both the UK’s MI5 and the US FBI made a rare joint statement in which they warned that the Chinese government was “set on stealing your technology using a range of tools”.
b) Nuclear espionage
This type of espionage was much more prominent in the 1990s-2000s. During that time, ongoing heated debates were taking place in the US with regards to what extent the significant progress of the Chinese nuclear weapons programme could be attributed to nuclear espionage. While there was no agreement as to how much was stolen and what impact it had on China’s programme, a team of scientists at the Los Alamos weapons laboratory concluded in 1995 that the advancement of China’s programme was probably fuelled by its espionage activities. With regards to the recent Chinese balloon scandal, the US government also noted that the balloon flew over sensitive locations housing nuclear weapons in Montana, which might indicate that China is interested in the status of the US nuclear arsenal and capabilities. Meanwhile, calls for talks on nuclear weapons are becoming more frequent due to the lack of discussions. As was stated by Bonnie Jenkins, US Undersecretary of State for international security and arms control, “the US has made little progress in establishing dialogues with China over its nuclear capabilities”.
c) Cyber espionage
China’s road to its prowess in cyber capabilities has been long, but has made stable progress. As stated by the MIT Technology Review, “China’s decade-long quest to become a cyber superpower is now paying off”. Since Xi Jinping came to power, this progress can be attributed to the PRC government’s very concentrated efforts to combine the activities of civilian and military organisations to enhance Chinese cyber capabilities. Winnona DeSombre, a research fellow at the Atlantic Council & Harvard’s Belfer Center, testified before Congress in 2022 with regards to China’s cyber capabilities. Five of the main points from her testimony best describe the current trajectory of China’s cyber power:
- China is a major peer and adversary in cyberspace; Chinese cyber capabilities rival those of the US, while its operations demonstrate the clear development of asymmetric capabilities that enable it to achieve its strategic goals, and its cyber defensive capabilities are robust.
- Xi Jinping has significantly escalated the Chinese rhetoric and capabilities around cyber power (such as remaking the international supply chain with Chinese companies).
- China has asymmetric capabilities that the US is currently constrained from developing via international or domestic law, on top of their already impressive arsenal that is used for both economic espionage and national security purposes.
- While both China and the US suffer from a cyber personnel shortage, China’s enablement of private sector offensive security contractors and academic institutions, and the emphasis on its asymmetric capabilities, will allow it to grow these capabilities despite the current issues.
- The US does not currently have adequate cyber defences, personnel, supply chain security, or international technical and standards leadership to rival China on a long-term basis.
Recently, TikTok, the hugely popular video-sharing platform developed in China (in China, the domestic version of the app is called “DouYin”) came under an immense spotlight. The main concerns that were shared among an increasing number of countries concerned the application’s ability to collect huge amounts of personal data that, if requested by the Chinese government, could be acquired from ByteDance, its parent company based in China. This potential data access has raised significant national security concerns; therefore, it is forcing governments to take more drastic action.
On 23 March, TikTok’s CEO Shou Zi Chew faced almost five hours of questioning at a US congressional hearing. The main concern voiced by the Committee members was that TikTok’s operations in the US pose a national security threat due to the related data being potentially accessible by the CCP, which could be used to track American citizens and government institutions. While Shou insisted that the company is taking measures to guarantee data safety, including the establishment of a new subsidiary – TikTok U.S. Data Security – that would ensure all US data is secured and stored in US-based servers run by Oracle, these assurances did not dissuade the Committee members.
While banning TikTok is often perceived as almost imminent, such an outcome (banning a popular communications tool) would be virtually without precedent (Trump attempted to ban it, but failed). The actual technical and legal ability to enforce such a decision is limited; therefore, in a case where concrete actions were taken to ban TikTok, an almost definite legal battle would be triggered on the grounds of free speech (The First Amendment). However, the Restricting the Emergence of Security Threats that Risk Information and Communications Technology (RESTRICT) Act, a bipartisan bill introduced in the Senate earlier this month, is more likely to pass. It could provide a way forward to potentially restricting or prohibiting TikTok from conducting business in the US.
The dangers posed by TikTok are being taken seriously by other countries as well. While India (and Afghanistan since 2022) already imposed a nationwide ban on TikTok and several other Chinese apps in 2020, other countries are proceeding more cautiously and are only imposing bans on the application’s use for government officials. EU institutions are also advised their staff to avoid using TikTok. The fate of TikTok remains unclear; however, it is evident that there will be a long and cautious battle, due to justified concerns about China’s willingness to use its weaponised dependence and other tools of coercion to dissuade other countries from taking action.
d) Academic espionage
In recent years, Chinese espionage and intel-gathering activities in the academic sphere have also gained significant attention. Currently, mitigating risks of foreign activities in the US universities has become a major topic for the US government and its agencies to address. In this case, China is again a significant focal point. According to the FBI report, “Foreign adversaries exploit America’s deeply held and vital culture of collaboration and openness on university campuses, with the Chinese government posing a particular threat to US academia”.
Recently, US Senator Ted Cruz introduced a bill to address foreign threats to higher education in the US (the “Stop Higher Education Espionage and Theft Act of 2023”). While the Bill does not explicitly mention China, during his introduction Cruz stated that “China is the single greatest geopolitical threat facing the US, and the CCP exerts a profoundly malign influence on our university campuses”. Another point of contention between the two countries is related to the network of China’s Confucius Institutes. Over the last five years, as a result of several cases of close links with the CCP and attempts to impose academic censorship, in the US alone, most of the Institutes have closed down. However, there are increasing efforts from academia to regulate the CI’s activities in a manner that would allow their partial return. In a recent report, published by The National Academies of Sciences, Engineering and Medicine Committee, it was acknowledged that such institutes posed a potential risk; however, it did not find substantial evidence “at the unclassified level” to back up such allegations. Instead, the Committee proposed a set of criteria that must be met in order for the Confucius Institutes to continue their operations. Nevertheless, the fate of the Institutes currently remains unclear.
Difficult road ahead
Chinese espionage activities are notably on the rise, and the actions being taken are becoming more sophisticated and covert, with more potential to do significant harm. China’s upper hand in the cyber security sphere indicates a worrisome trend that is likely to remain one of the focal points of bilateral contention between the US and China. Moreover, the efforts to curb Chinese espionage activities are now being highly prioritised: in October 2021, Central Intelligence Agency (CIA) announced the creation of the China Mission Centre to “address the global challenge posed by the PRC that cuts across all of the agency’s mission areas”. Furthermore, high-level bilateral meetings are consistently raising the issue of cyber theft and cyber security. New instances of large-scale China-related espionage incidents in the US are now being taken very seriously, and often result in diplomatic standoffs (for instance, Blinken’s postponement of his visit to China due to the spy balloon incident).
Counterintelligence activities are of the utmost importance in order to fight the rise of Chinese espionage cases in the US. But the recent failures of the country’s intelligence network in China indicate that Chinese surveillance is becoming much more sophisticated. The US will be faced with an increasingly difficult road ahead, where it must decide how to effectively discern the intentions of the leadership in a country where the power is significantly concentrated in Xi’s hands, surveillance is advanced and all-inclusive, crackdowns are widespread and the access to information is increasingly restricted.